Mathematical modelling: Cracking codes
View Sequence overviewWe need to interpret our mathematical results in context to determine what these results mean in practice. We also need to evaluate our mathematical results in context to determine whether the solution provides an adequate and sensible answer to the real-world context.
Whole class
Cracking codes PowerPoint
Each group
Frequency analysis Spreadsheet
Each student
Digital copy of Encrypted text Student sheet
Cracking codes Student sheet
Task
Show slide 9 of Cracking codes PowerPoint. Explain that students have investigated the problem in context, formulated a mathematical problem, and solved the problem to give a mathematical result. Now they need to interpret their mathematical results in context to determine what these results mean in practice.
Revise the different strategies that students have used up to this point in the sequence, including letter frequencies, common words, and common letter patterns.
Divide students into small groups and provide each group with access to the Frequency Analysis spreadsheet. Also provide students with Encrypted text Student sheet, which includes encrypted pieces of text to decipher and instructions on how to use the Find and Replace function in Microsoft Word as a tool to efficiently substitute letters.
Explain to students that a substitution cipher has been used to encrypt the different passages of text, and they will need to use their deciphering strategies to decode the texts. Encourage students to use the Analysing frequency spreadsheet. To decipher the codes, students will need to use letter frequency in conjunction with other deciphering strategies they have used throughout the sequence.
The Find and Replace function in Microsoft Word will search a document, find all instances of specified text, and replace it with alternate text.
Depending on your process for deciphering text, you may need a way to distinguish between the parts of the ciphertext that you have already decoded and the remaining encrypted text.
One way to do this is to format your decoded text differently to the original ciphertext.
Paste encrypted text into a new Word document. Open Find and Replace which can be found in the editing tools on the Home ribbon (or by using the Ctrl-H shortcut). | 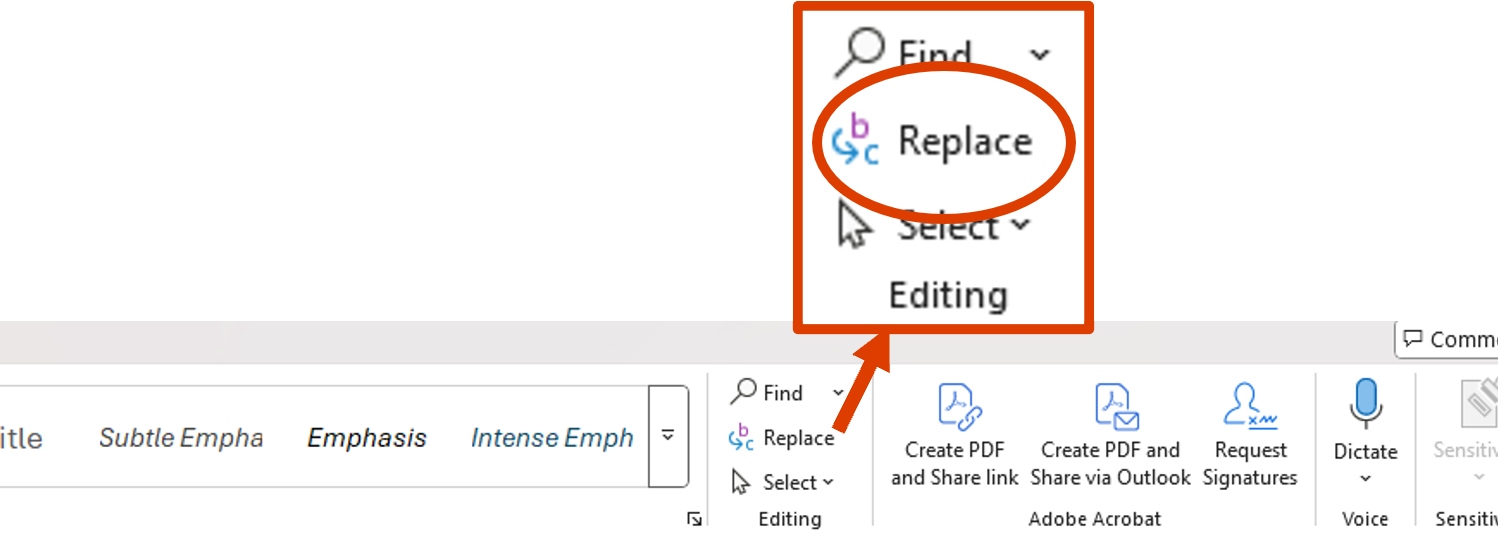 |
Setting the font format of the ciphertext Ensure your curser is in the Find what box, then click on More > > > Format > Font.... This allows you to set the format of the font of the original ciphertext that you paste into Word. Only text formatted in this way will be searched. | 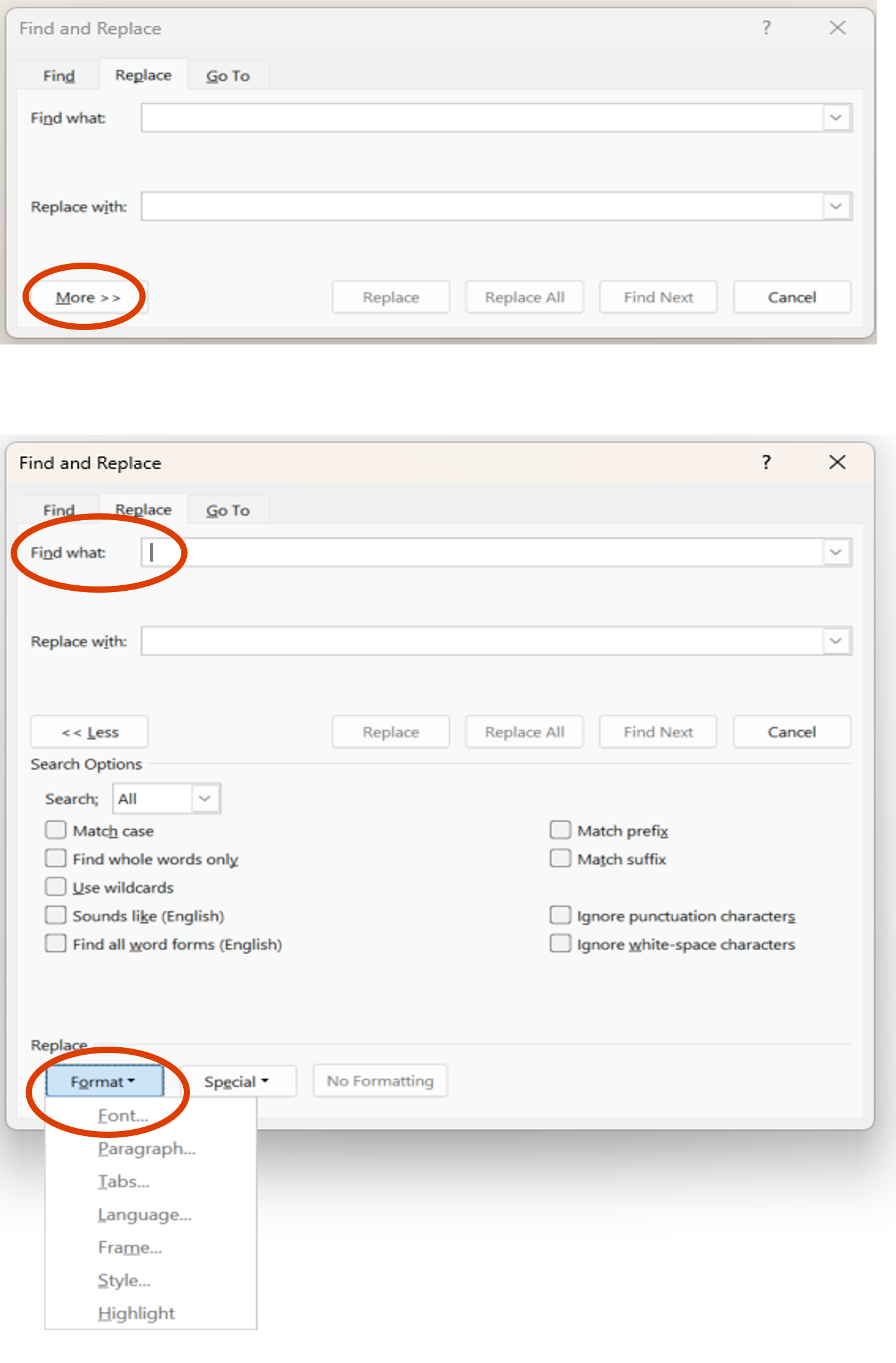 |
| Set the font style and colour to match the format of the ciphertext. In most cases the font style will be Regular and the colour will be Automatic. Then click OK. | 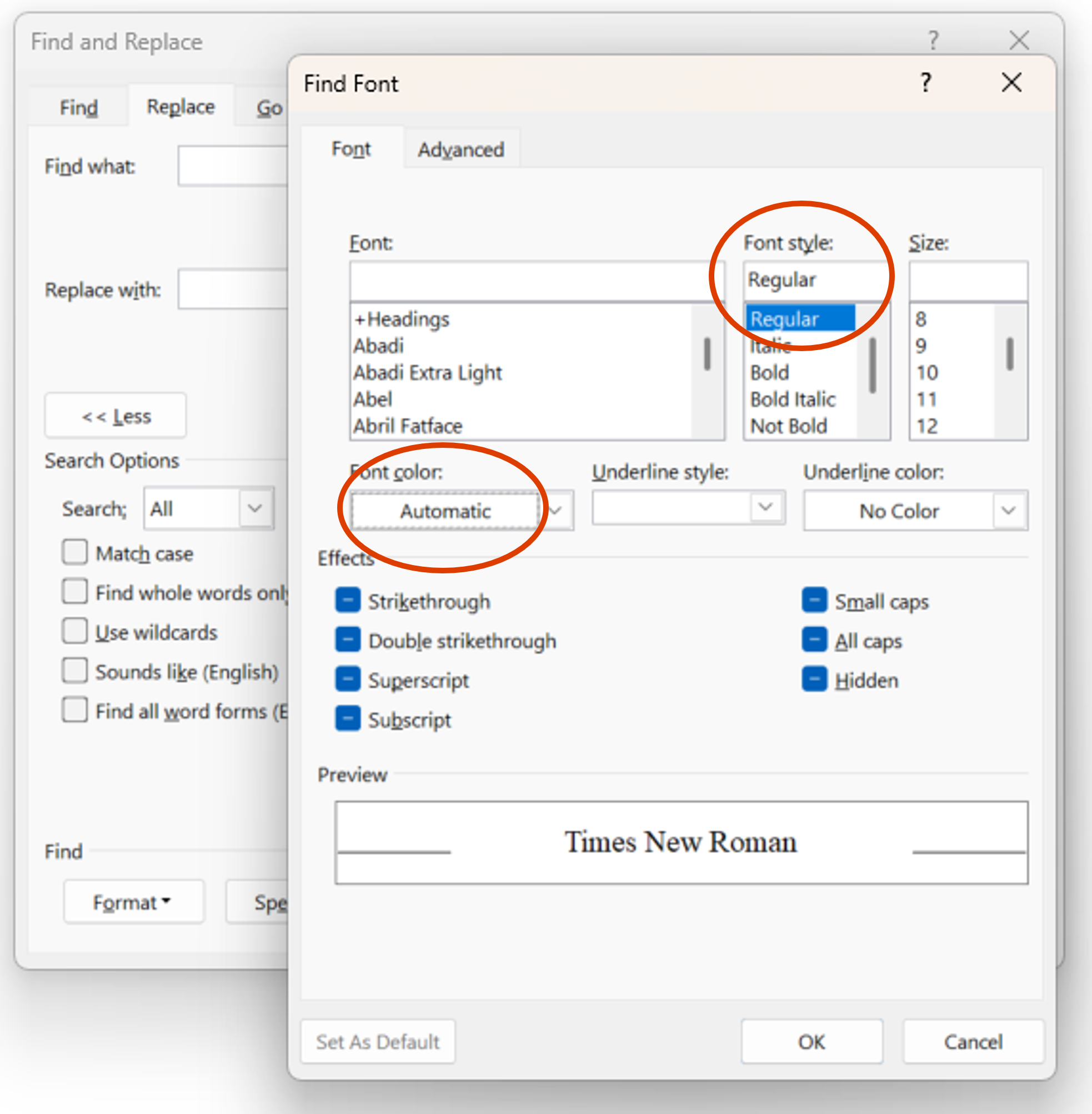 |
Setting the font format of the deciphered plaintext Next, ensure your cursor is in the Replace with box and click Format > Font. Set the font formatting for the replacement plaintext. Make sure it stands out! For example, bolding the text and changing the colour will help distinguish this text. Click OK. | 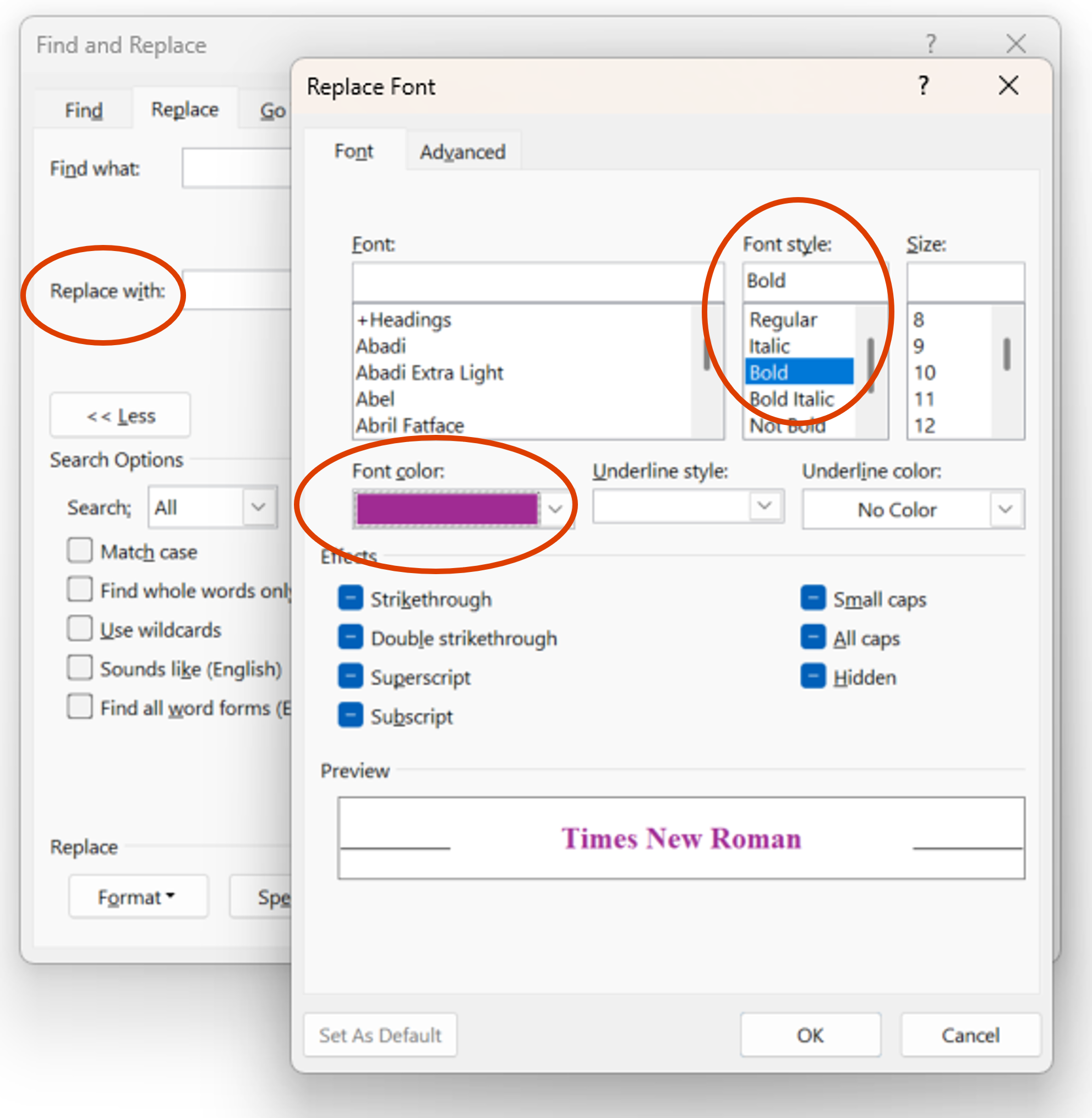 |
| You will see the format of the font now for the text that will be searched and the replacement text. | 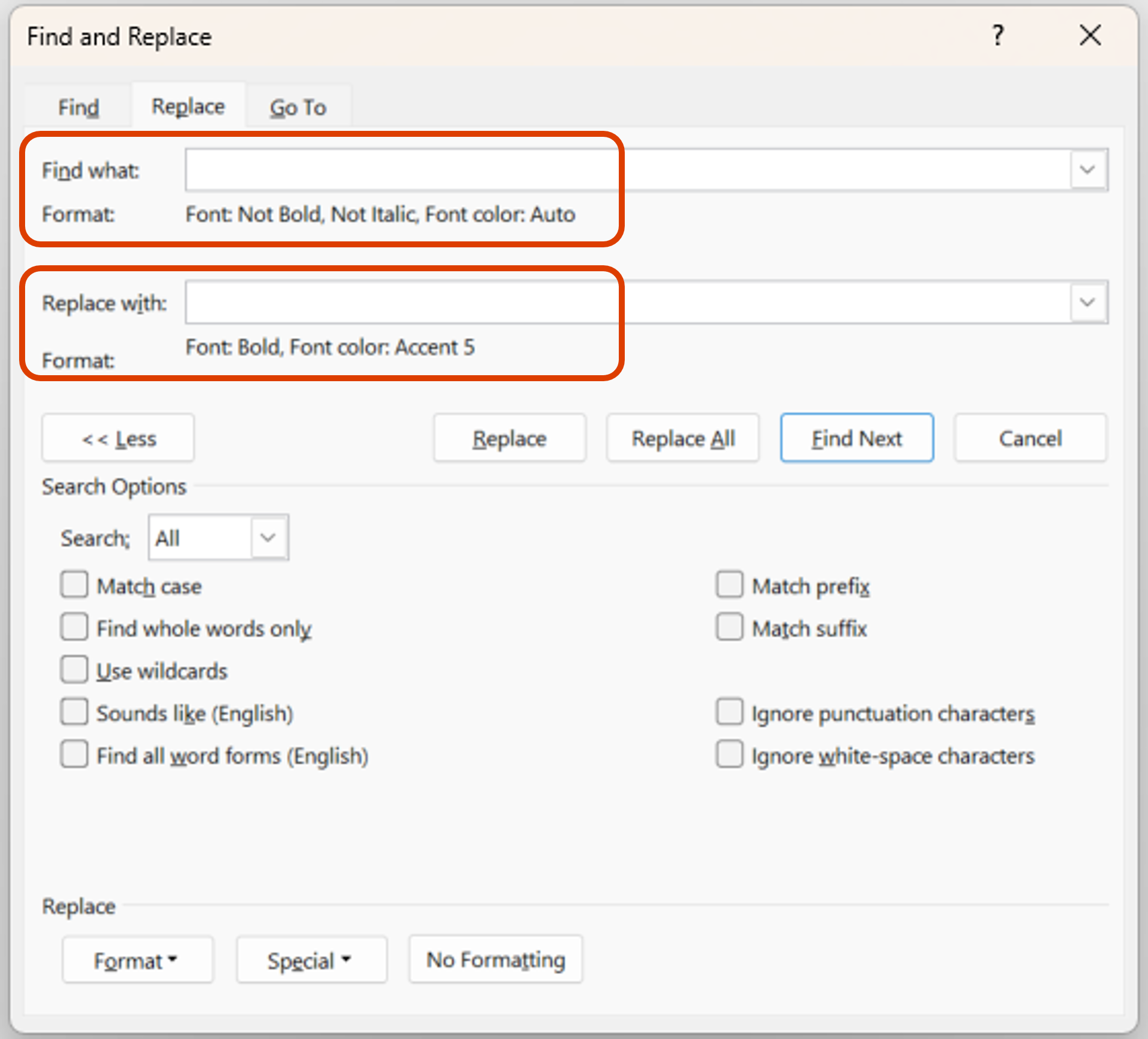 |
| Use your deciphering strategies such as letter frequency, common words, and letter patterns to change letters in a coded piece of text. Your decoded text will stand out from the ciphertext to help you decide on which letters you would like to substitute. | 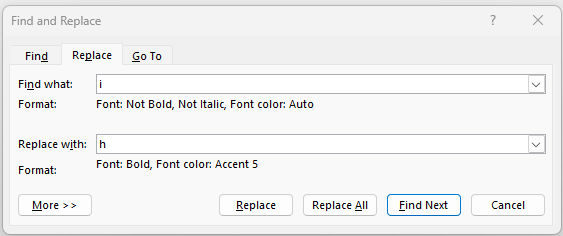
 |
The students need to decipher four different codes. The codes range in length and the genres of each text is different. Each ciphertext uses a different substitution cipher.
Ciphertext 1 - From Harry Potter and the Philosopher’s Stone
| Plaintext | A | B | C | D | E | F | G | H | I | J | K |
| Ciphertext | E | J | A | L | Q | R | C | P | D | W | I |
| L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| O | X | K | V | U | B | T | N | M | F | S | H | Y | Z | G |
Harry tried. And tried. He had no idea what Mr Ollivander was waiting for. The pile of tried wands was mounting higher and higher on the spindly chair, but the more wands Mr Ollivander pulled from the shelves, the happier he seemed to become.
“Tricky customer, eh? Not to worry, we’ll find the perfect match here somewhere – I wonder now – yes, why not – unusual combination – holly and phoenix feather, eleven inches, nice and supple.”
Harry took the wand. He felt a sudden warmth in his fingers. He raised the wand above his head, brought it swishing down through the dusty air and a stream of red and gold sparks shot from the end like a firework, throwing dancing spots of light on to the walls. Hagrid whooped and clapped and Mr Ollivander cried, “Oh, bravo! Yes, indeed, oh, very good. Well, well, well… how curious… how very curious…”
He put Harry’s wand back into its box and wrapped it in brown paper, still muttering, “Curious… curious…”
“Sorry,” said Harry, “but what’s curious?”
Mr Ollivander fixed Harry with his pale stare.
“I remember every wand I’ve ever sold, Mr Potter. Every single wand. It so happens that the phoenix whose tail feather is in your wand, gave another feather – just one other. It is very curious indeed that you should be destined for this wand when its brother – why, its brother gave you that scar.”
Ciphertext 2 - Short text
| Plaintext | A | B | C | D | E | F | G | H | I | J | K |
| Ciphertext | I | S | D | T | E | K | M | C | L | U | H |
| L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| P | R | Q | J | A | Z | F | Y | X | N | B | O | W | V | G |
The quick brown fox jumps over the lazy dog.
Ciphertext 3 – Passage on how Mary, Queen of Scots used cipher
| Plaintext | A | B | C | D | E | F | G | H | I | J | K |
| Ciphertext | X | Y | Z | A | B | C | D | E | F | G | H |
| L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| I | J | K | L | M | N | O | P | Q | R | S | T | U | V | W |
While imprisoned by her cousin, Queen Elizabeth the First, Mary, Queen of Scots used substitution ciphers to secretly communicate with her supporters about plans to escape and overthrow Elizabeth. In her ciphers, Mary replaced each letter of the alphabet with a different letter or symbol. The key to decoding the message was knowing the exact substitutions, which Mary shared with her supporters.
However, Sir Francis Walsingham, Elizabeth's spymaster, had a team of codebreakers who successfully deciphered Mary’s messages using techniques like frequency analysis. Through these decoded letters, they uncovered Mary's involvement in the Babington Plot to assassinate Elizabeth. This led to Mary's trial and execution.
Ciphertext 4 – Passage on distribution in statistics
| Plaintext | A | B | C | D | E | F | G | H | I | J | K |
| Ciphertext | H | U | M | T | G | A | N | F | B | V | O |
| L | M | N | O | P | Q | R | S | T | U | V | W | X | Y | Z |
| C | S | L | R | Y | I | Z | Q | J | X | K | E | W | P | D |
We analyse data to understand its variability. Reasoning about distribution is key to accounting for and describing variability. Distribution refers to the patterns of similarity and difference in data. Graphical displays and numerical summaries are used to explore, describe, and compare variability in distributions. Observations that relate to distribution could relate to spread (including range), shape, clumps, gaps, centre and atypical values.
Conduct a class discussion. Allow the students to share the different strategies that they use to decipher each piece of text.
Discuss: Which of the ciphertexts were easier to decode? Why?
- It is typically easier to apply letter frequency and word patterns to longer passages. Short passages are much harder to decipher.
- Context is also important. It is much easier to decipher code when you know the context of the original passage.
Provide students with Cracking codes Student sheet and allow time for students to individually complete this sheet.
This reflection can be used as a post-assessment of students’ learning throughout this sequence. This final question on this sheet asks students to create their own coded message. Allow students to share their code with others to decipher.